The Importance of Payment Authentication: Safeguarding Your Business

Table of Contents
- What is Payment Authentication?
- What is the Difference Between Payment Authentication and Authorization?
- What Does it Mean to Authenticate a Transaction?
- How Do I Authenticate a Payment Method?
- Can Banks Verify Authenticity?
- How Paystand’s Payment Authentication Solutions Protect Your Bottom Line
Key Takeaways
- Payment authentication verifies the identity and legitimacy of payment transactions, which is particularly crucial in B2B payments to prevent fraud and chargebacks.
- Payment authentication differs from payment authorization. Authentication confirms the purchaser's identity, while authorization ensures the payment method can cover the transaction.
- Authentication methods include AVS, CVV, CHAP, 3DS, and tokenization, each offering varying levels of security and protection against fraud.
- Banks play a vital role in authenticating transactions through passwords, PINs, 2FA, biometric authentication, chip and PIN technology, transaction monitoring, and encryption.
Protecting your business from payment fraud is crucial, and there are steps you can take to ensure a safe and secure financial environment. You can avoid potential losses and maintain your company's transaction integrity by staying vigilant.
Experts estimate global losses from card fraud to reach nearly $400 billion over the next decade. According to a recent study, each fraudulent transaction costs U.S. businesses an average of $3.75. But it's not all bad news. By prioritizing payment authentication, you can significantly reduce these costs and protect your company's financial well-being.
In this article, we’ll explore the difference between payment authentication and payment authorization, learn how payment authentication works, and discover a practical solution to avoid the high costs associated with poor authentication practices.
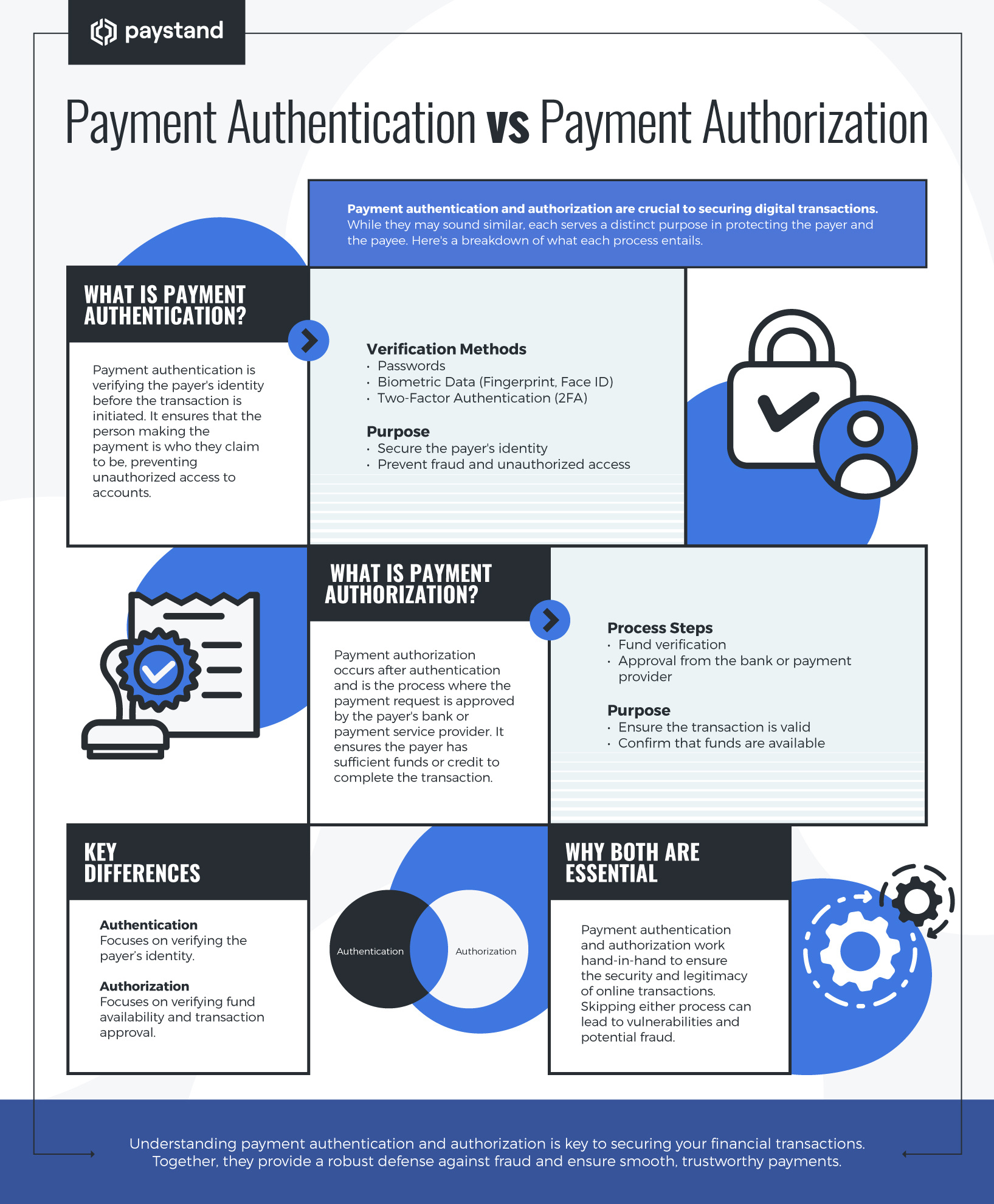
What is Payment Authentication?
Transactions tend to be higher in B2B payments, so it’s even more important to authenticate them. Payment authentication refers to verifying a payment transaction’s identity and legitimacy.
Ensuring that the person or business initiating the payment is the authorized account holder or cardholder is crucial. Authentication also helps to protect merchants from chargebacks, fraud, and other unauthorized activities.
What is the Difference Between Payment Authentication and Authorization?
While payment authentication and authorization are important to ensure smooth transactions, the two terms convey different meanings and challenges.
With authentication, the purchaser is responsible for providing adequate proof that they have the right to purchase using the method at issue. To do this, the purchaser must offer information to verify that they are the legitimate cardholder and not an impersonator attempting to misappropriate the legitimate card owner’s identity to perpetrate an unauthorized transaction.
On the other hand, payment authorization is a necessary step that follows the payment authentication. When you authorize a payment, you take steps to verify that the payment method being used — such as a credit or debit card — is a vehicle that can relay sufficient funds to cover the transaction. Payment authorization aims to ensure that the payer has enough money to complete the transaction and that the payer’s bank doesn’t decline the payment method.
What Does it Mean to Authenticate a Transaction?
Pay authentication requires that your clients present evidence to prove their identity. For instance, they may be asked to provide a username and a password, answer screening questions, or provide a fingerprint or face scan. Sometimes, a person can be authenticated through the information provided by the device they are using.
How Do I Authenticate a Payment Method?
Several methods are available for authenticating payment methods, each with advantages and disadvantages.
- Address Verification System (AVS): It validates billing addresses by comparing them with bank or credit card records to prevent fraud. AVS gives payees control over payment approvals and investigations but is vulnerable to hackers who can easily find addresses online. Therefore, AVS should be used with other authentication systems.
- Card Verification Value (CVV): These authenticate credit or debit card transactions when the physical card is absent. This prevents fraudulent use of a card number but not the unauthorized use of a stolen card.
- Challenge-Handshake Authentication Protocol (CHAP): This device-driven authentication system periodically re-authenticates users during an online session. It uses a shared secret as an access point, ensuring that the original user is not interfered with by third parties who have stolen their credentials. CHAP works best when combined with other payment authentication methods.
- 3-D Secure (3DS): It authenticates digital payments by relaying payment and contextual information to banking institutions for identity verification. It is a risk-based payment authentication method that uses multiple data points.
- Tokenization: It replaces sensitive payment information with a unique token. This token is then used to process the transaction without exposing the card number to the merchant. Tokenization is a secure authentication method preventing fraudsters from obtaining the customer's card number even if they can intercept the transaction data. However, merchants must implement additional security measures to protect the tokens themselves.
Can Banks Verify Authenticity?
Banks play a crucial role in ensuring transaction authenticity and safeguarding financial systems' integrity. However, with sophisticated financial crimes rising and banking operations becoming more complex, verifying transaction authenticity has become more challenging.
Banks face ongoing challenges in verifying authenticity despite these efforts due to the evolving nature of financial crimes and the increasing use of digital channels for transactions. However, by continuously innovating and adopting new technologies, banks enhance their ability to detect and prevent fraudulent activities, ensuring financial systems' integrity and security.
How Do Banks Authenticate Transactions?
Banks employ a range of sophisticated measures to authenticate transactions and ensure the security of their customers' funds. Here are some common authentication methods used by banks:
- Passwords and PINs: Customers are typically required to create a unique password or personal identification number (PIN) when setting up their bank account. This password or PIN is used to verify the customer's identity when accessing their account online or through a mobile banking app.
- Two-Factor Authentication (2FA): 2FA adds an extra security layer by requiring customers to provide two identification forms when logging in or making a transaction. This can include a password combination, a code sent to the customer's mobile phone via SMS or an authentication app, or a biometric scan such as a fingerprint or facial recognition.
- Biometric Authentication: Some banks offer biometric authentication options, such as fingerprint scanning or facial recognition, as an alternative to passwords or PINs. These methods rely on the customer's unique biological characteristics to verify their identity.
- Chip and PIN Technology: Banks often use chip and PIN technology for in-person transactions using a debit or credit card. This involves inserting the card into a card reader and entering a PIN to complete the transaction. The chip on the card contains encrypted data to verify the card's authenticity and prevent counterfeiting.
- Transaction Monitoring: Banks continuously monitor customer transactions for suspicious activity, such as large or unusual purchases or transfers. The bank may contact the customer to verify the transaction or take additional security measures if suspicious activity is detected.
- Encryption: Banks use encryption technology to protect customer data and communications. This ensures that sensitive information, such as account numbers, passwords, and transaction details, is kept confidential and secure.
How Paystand’s Payment Authentication Solutions Protect Your Bottom Line
Maintaining and building your business depends on incorporating a dependable and robust payment authentication process into your accounts receivable protocols. Paystand’s advanced B2B payments platform makes it possible to digitize receivables, automate processing, reduce time-to-cash, eliminate transaction fees, and enable new revenue, all in a state-of-the-art secure environment incorporating the most robust financial authentication protocols.